Remember watching circus shows on TV? Do you recall seeing the magician pull out a rabbit from their hat? How about making a single currency note become two before your very eyes?
The rabbit stunt could pass for a trick but the stunt with currency notes? We’ll soon that it could very well pass for fraud. Follow us as we dive into this insightful article on double-spending.
What is Double Spending?
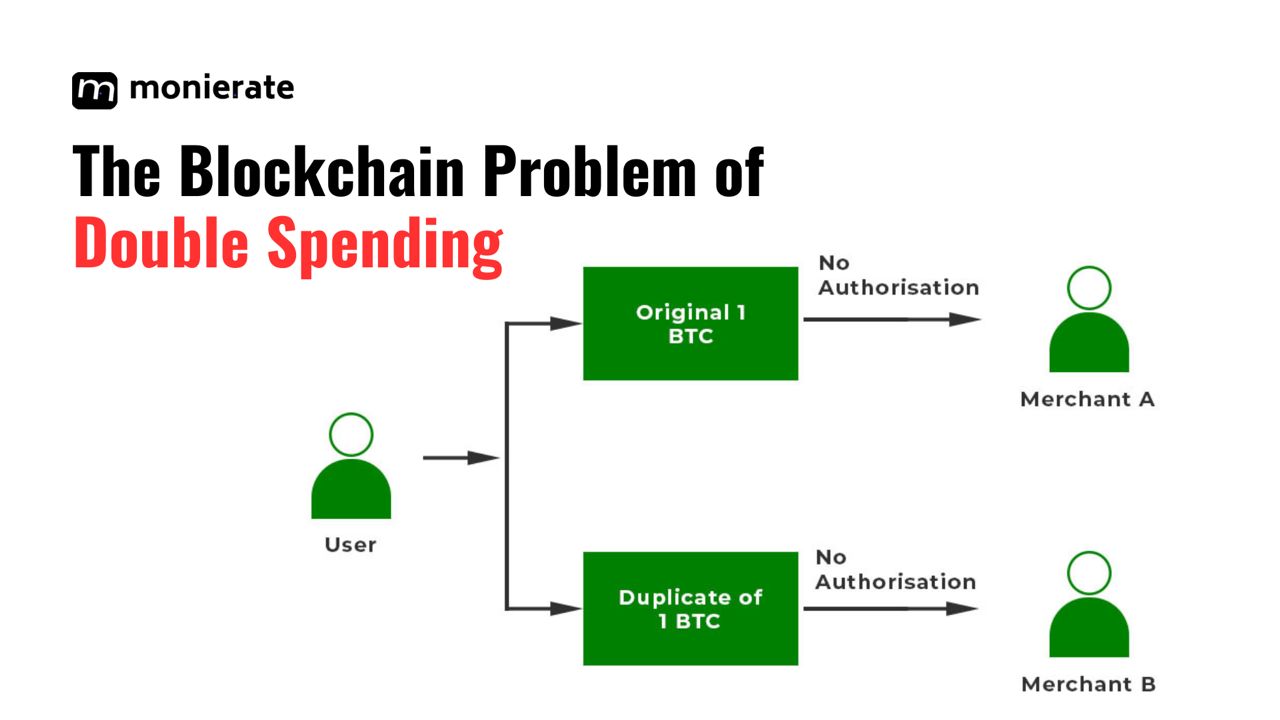
Double-spend is a situation where conventional money or cryptocurrency is spent twice. It involves reusing an exact same bill or token.
Imagine it this way. Someone wants to buy two items that are worth 100 naira each. However, they’re doing so with a single NGN 100 note.
Sounds impossible, right? So how do they get about it?
The answer is counterfeits.
The fraudster makes identical copies of the authentic note. They then go ahead to purchase items with both real and counterfeit notes. This is the basic idea of what double spending is.
Essentially, our imaginary fraudster would be spending their original NGN 100 note more than once.
How Double Spending Attacks are Conducted
Two things can happen in a double spend. One is that the spender illegally duplicates a currency. This allows them to spend the fake currency/token in one instance. They could then use the genuine copy in another instance.
Double spending cash duplicates obviously only happen in a cash system. The success of this is based on inadequate validation. Unrelated, but verification can include touch/feel, scanning with UV lights, and more.
The second way double spending occurs is through system manipulation. This is peculiar to digital platforms. Attackers in such a scenario transfer a single token multiple times.
They may do so all at once or at several instances.
Double spending in digital cash systems is a critical problem. Its success is based on synchronisation issues, inadequate fraude detection, etc.
Double Spending in Financial Ecosystems
We know banks and we know blockchain. We know that banks fall under conventional finance. Also, we know that blockchain is the revolutionary version of this.
Both banks and blockchains face some common challenges. As you might guess, an example is double spending. This section expands on the occurrence of double-spending in each financial ecosystem.
Double-Spending in Traditional Finance
Double spending began in traditional finance. The problem exists with both physical and digital cash systems. It is, however, less of an issue in the former than the latter.
Physical cash can be double-spent. Why? Because paper money can be duplicated. This is true, even though it is a difficult feat.
The attacker will need access to specialised equipment. They’ll also need the right kind of paper. Regular people don’t get their hands on those so easily. Moreover, one cannot technically double spend paper cash since one cannot use it twice.
What that means is that they no longer have the cash for spending once they exchange it for a product or service.
The problem takes a different turn in traditional digital cash systems. In fact, these systems are prone to double-spending attacks.
Attackers here are known for raking serious havoc. They may duplicate the codes that make up their digital assets. This has the effect of duplicating the money in their accounts.
Alternatively, attackers may send the same asset to multiple recipients. Only that they do so all at the same time. This, right here, is the actual crime in focus.
It is equivalent to using the exact same currency note for simultaneous payments.
Double-Spending in Blockchain
Blockchain or decentralized finance is a lot safer. First off, this system was designed to combat double-spending. Unfortunately, it is not completely impregnable.
Double spending attacks are still possible on a blockchain. The problem is rare and happens far in between. Most often, this is conducted through a race attack, a Finney attack, or a 51% attack.
Here’s an illustration:
Race Attack
A race attack involves making two conflicting transactions. These transactions are initiated at nearly the same time. The goal here is to get one transaction verified and the other rejected.
An attacker might spend coins at a physical location. While their payment is being processed, they proceed to broadcast a conflicting transaction to the network. The intention with this is to have the second transaction accepted and the first one rejected.
Finney Attack
Finney attacks are more technical than race attacks. They involve careful planning and tactics. Here, an attacker first pre-mines a block that contains a double spend transaction.
They then make a transaction on the blockchain. Once made, they broadcast the pre-mined block to the network. In the event that the network fails to catch the problem with the pre-mined block, the double-spend attack may be successful.
51% Attack
A 51% attack involves conquering a blockchain. By this, an attacker gains majority control of the computational power. This allows them to reverse transactions or even create a fork.
For instance, an attacker might spend their coins in one transaction. After that, they use their majority control to invalidate the transaction. They, therefore, reverse transactions made in a past block and end up double spending coins.
How Double Spending Is Handled
Double spending occurs in different ways within a blockchain. Each of these scenarios is handled distinctly. In this section, we outline the ways in which double spending occurs and how they are handled:
A double-spend involves two transactions entering a network. However, they often occur at different endpoints. If this happens, both transactions may be rejected when the next block is mined.
There’s another way this scenario can be handled. It is that the next mined block contains one transaction. All subsequent blocks containing the second transaction is then rejected.
The third scenario is less likely. Nevertheless, it still exists as a possibility. It involves two blocks mined simultaneously with each containing one of the two double-spend transactions.
Having two blocks formed like this could create a fork. The network can decide on the right chain to continue on using a consensus. Next, the validity of the chosen chain is strengthened with increasing block confirmations.
How to Check Double-Spend Attacks
Blockchain confirmations. That’s the simple answer. Confirmations in blockchain help increase integrity.
Essentially, it is the best way to check double spend attacks. The idea is that having more and more block confirmations reduces the chances of an alteration to existing data.
Conclusion
Digital financial systems are under so much heat. Remote bank heists happen every other month. These attacks lead to losses that run into millions.
Sadly, there’s also the issue of double spending.
The latter poses a problem to the economy. It reduces the confidence and usability of a financial system, potentially crippling it. If this situation goes unchecked, the value of the currency within such systems might be significantly eroded.

